 Internet Computer (ICP)
Internet Computer (ICP)
$2.541 +5.26% 24H
- 78Chỉ số cảm xúc xã hội (SSI)+21.16% (24h)
- #38Xếp hạng nhịp đập thị trường (MPR)+69
- 15Đề cập trên mạng xã hội 24h+50.00% (24h)
- 73%Tỷ lệ tăng KOL 24h9 KOL đang hoạt động
- Tóm tắt
- Tín hiệu tăng giá
- Tín hiệu giảm giá
Chỉ số cảm xúc xã hội (SSI)
- Tổng quan dữ liệu78SSI
- Xu hướng SSI (7 ngày)Giá (7 ngày)Phân bổ cảm xúcCực kỳ lạc quan (40%)Tăng giá (33%)Trung tính (13%)Giảm giá (7%)Cực kỳ bi quan (7%)Thông tin chuyên sâu SSI
Xếp hạng nhịp đập thị trường (MPR)
- Thông tin chuyên sâu về cảnh báo
Bài đăng trên X
- Xu hướng của ICP sau khi phát hànhTrung tính
- Xu hướng của ICP sau khi phát hànhTăng giá
 markus.ai.icp∞☕️ Dev OnChain_Analyst A1.91K @markus_AI_ICP
markus.ai.icp∞☕️ Dev OnChain_Analyst A1.91K @markus_AI_ICP markus.ai.icp∞☕️ Dev OnChain_Analyst A1.91K @markus_AI_ICP9 1 167 Gốc >Xu hướng của ICP sau khi phát hànhTăng giá
markus.ai.icp∞☕️ Dev OnChain_Analyst A1.91K @markus_AI_ICP9 1 167 Gốc >Xu hướng của ICP sau khi phát hànhTăng giá- Xu hướng của ICP sau khi phát hànhCực kỳ lạc quan
 CRYPTO FRONT TA_Analyst Trader S8.41K @cryptofrontio
CRYPTO FRONT TA_Analyst Trader S8.41K @cryptofrontio Egzon Fejzullahi D817 @EgzonFejzullahi
Egzon Fejzullahi D817 @EgzonFejzullahi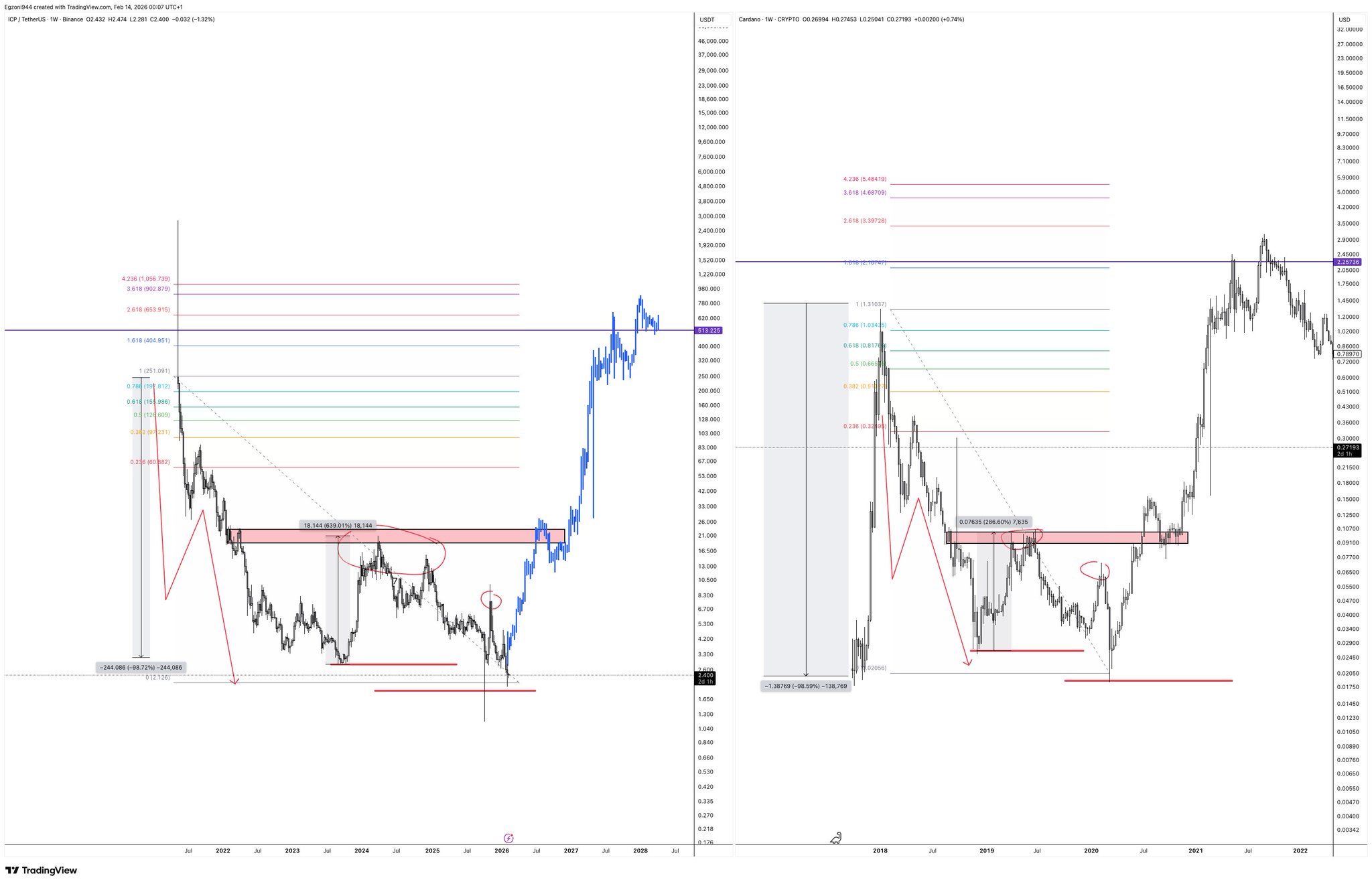 40 1 940 Gốc >Xu hướng của ICP sau khi phát hànhTăng giá
40 1 940 Gốc >Xu hướng của ICP sau khi phát hànhTăng giá ∞ ICP Jay Nolan ∞ Influencer Community_Lead B1.92K @CambrinNolan
∞ ICP Jay Nolan ∞ Influencer Community_Lead B1.92K @CambrinNolan Ihtisham Ul Haq D1.56M @iihtishamm
Ihtisham Ul Haq D1.56M @iihtishamm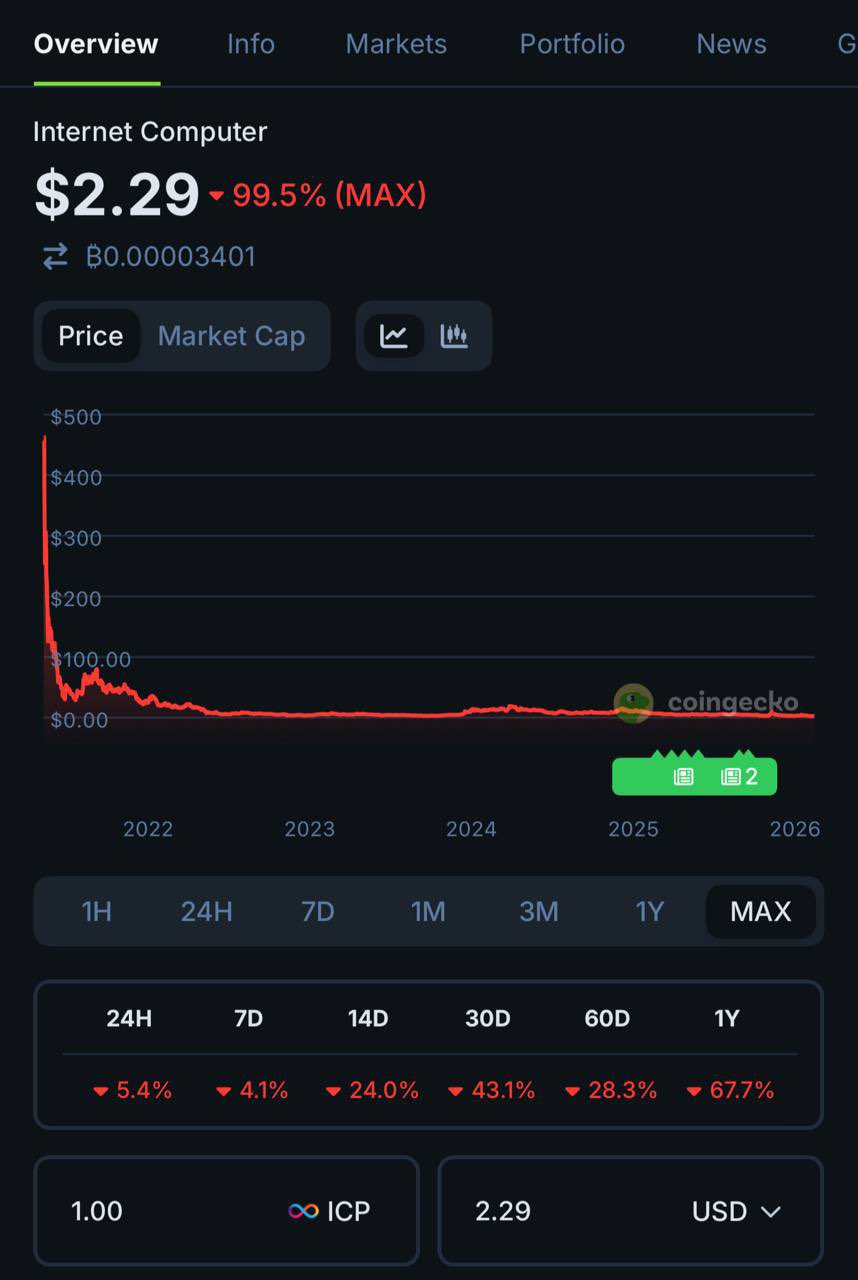 17 0 404 Gốc >Xu hướng của ICP sau khi phát hànhCực kỳ bi quan
17 0 404 Gốc >Xu hướng của ICP sau khi phát hànhCực kỳ bi quan- Xu hướng của ICP sau khi phát hànhTăng giá
- Xu hướng của ICP sau khi phát hànhTrung tính
- Xu hướng của ICP sau khi phát hànhCực kỳ lạc quan
 Grim Trader Influencer A1.41K @Grim_siv
Grim Trader Influencer A1.41K @Grim_siv dom williams.icp ∞ D220.53K @dominic_w1.17K 114 55.94K Gốc >Xu hướng của ICP sau khi phát hànhTăng giá
dom williams.icp ∞ D220.53K @dominic_w1.17K 114 55.94K Gốc >Xu hướng của ICP sau khi phát hànhTăng giá